IT Micron
No Breaches. Zero faith. Nothing is down.
The reality of modern cyberwarfare has shown that no vendor can stop zero-day malware from entering your network and endpoints; however, our proprietary technology is specifically designed to stop any harm.
DRAGON ENTERPRISE

ENDPOINT

ENDPOINT

ENDPOINT

ENDPOINT

ENDPOINT
Zero Downtime. Zero Damage.
Multi-Tenant
Capabilities
Enable MDR Capabilities
Patented Auto Containment
Centralized Platform
Scalable Protection
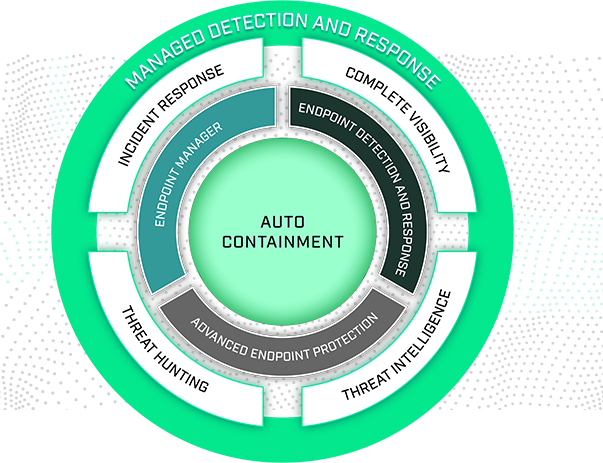
The Importance of Zero Dwell Time
It's critical to be aware of the fact that detection-based solutions can never completely stop all known good or criminal activity when it comes to protecting your enterprise endpoints. Unknown files may be absolutely safe and necessary for system operation, or they may be deadly APTs or zero-day attacks that result in major breaches. Your cyber security program must be able to distinguish between the two in order to stop breaches and boost productivity. Unlike other security methods available today, themicronit's patented auto-containment technology eliminates zero-day assaults with no negative effects on the end user experience.

Prevent your damage impact
Find today's cyber risks before they become tomorrow's ransomware. Protecting your environments with 100% effectiveness will enable your endpoints, network, and workloads.

Cloud-Based
Security Updates
Put the most recent threat intelligence against cyber threat signatures and payloads on every endpoint, network, and workload.

Protect Against Unknown Threats
Using strong static, dynamic, and patented behavioural AI, defence against brand-new or
zero-day cyber attacks.

Patented Auto Containment™
Our minimal Kernel-level API virtualization can protect your endpoints from unforeseen cyberattacks that could harm them.

Attack Chain Visualizations
Discover the full context of an attack to put the pieces together on how hackers are trying to
infiltrate your network.
As opposed to identifying threats, stop breaches at the source.
Find today's cyber risks before they become tomorrow's ransomware. Protecting your environments with 100% effectiveness will enable your endpoints, network, and workloads.
Forensic
Scan Tool
Security
Scorecard
Real-time
Threat Map
Open-Source
EDR
RESPONSIBLE BREACH PREVENTION FOR VERIFIED ORGANIZATIONS
Customer security is our top priority. Through extensive testing, global industry leaders have endorsed our endpoint security solutions. They rely on themicronit's unique auto containment, which neutralizes ransomware, malware, and cyberattacks, to prevent breaches. Every day, the Dragon Platform defends millions of endpoints against online dangers.

Superiority in the industry
Leading industry associations, authorities, and experts have acknowledged the value of MicronIT solutions and services. Our cutting-edge technology are safeguarding businesses all across the world.

Endpoint Protection
100% defence against web and email threats as well as 0-day malware attacks.
100% in the detection of the pervasive and common malware found in the recent 4 weeks.
Malware Protection
MicronIT Advanced Endpoint Protection can stop malware and defend against unfamiliar files.

Endpoint Protection
Endpoint Protection Platform Receives 4.3/5
83 percent endorse MicronIT
Technology and security
Administration Platform
Best Managed Security Service for the 2018 Trust Award
2019
Threat Intel Technology Finalist
Endpoint Protection 60x |
Firewall Awards
Endpoint Protection Platform: 4.2 out of 5
Rating of 4.3/5 for Advanced Endpoint Protection
Endpoint Detection and Response Receives 4.5/5
